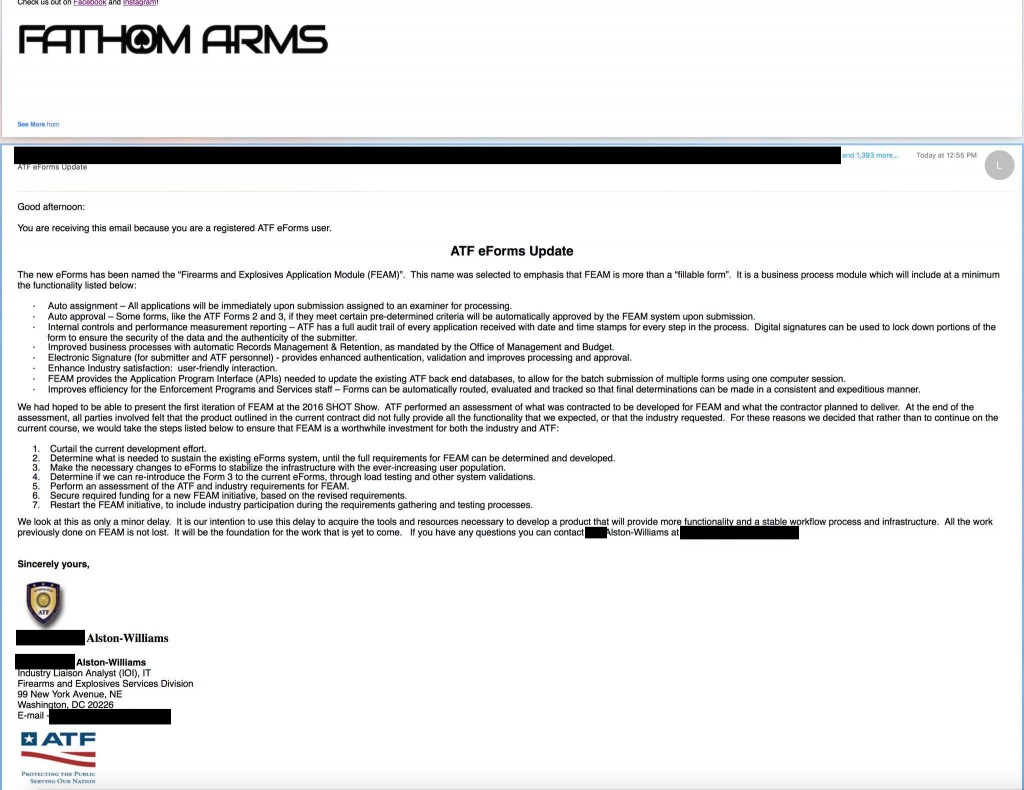
In a snafu of epic proportions, a representative of the ATF has inadvertently released the email addresses of 1,400+ eForms users. It is conceivable that this list of email addresses can be compared to existing hacked information and provide more personally identifying information of these citizens. This email is also only listing G-H, so it’s possible that many more email addresses have been released. With over 10,000 eForms users that could be a large amount of Americans. Couldn’t lists like this be considered gun registries?
ATF’s eForms allows individuals and members of the firearms industry to file certain forms electronically rather than via paper applications. The electronic filing is designed to be more efficient and accurate and will allow ATF to process the submissions more efficiently. The forms that can be filed relate to the importation of firearms, ammunition and implements of war; transactions with National Firearms Act (NFA) firearms; and the annual firearms manufacturing report.
The email was intended to be a notification of a new version of eForms called the FEAM. The new system is intended decrease the amount of time take to approve an eForm. As we’ve seen with ‘other’ government website projects, it’s late and now they are scrambling to make eForms suitable until FEAM can be released.
Talk about last minute, this was supposed to be presented at SHOT Show 2016 the week of January 17th.
We’ve all made email mistakes, but when we are talking about NFA items, the ATF may have just put a target on the back of these law abiding folks.


You must be logged in to post a comment.